Review RMS Users
Audit the Users setup in RMS.
Users and their assigned Security Profiles determine who can access your RMS database and what actions they can perform once they have logged in.
System Administrators should regularly review the active users in RMS and their assigned Security Profiles to protect the sensitive information stored in the RMS database.
-
Begin
- Add Button
Active Users
System Administrators should regularly review the active users in RMS and their assigned Security Profiles to protect the sensitive information stored in the RMS database.
Have your System Administrator complete the following.
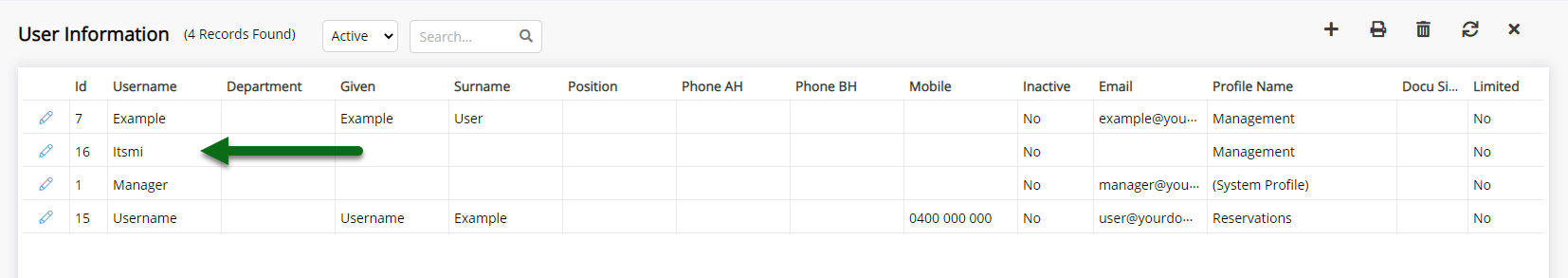
Go to Setup > Users > User Information in RMS and select the View 'Active'.

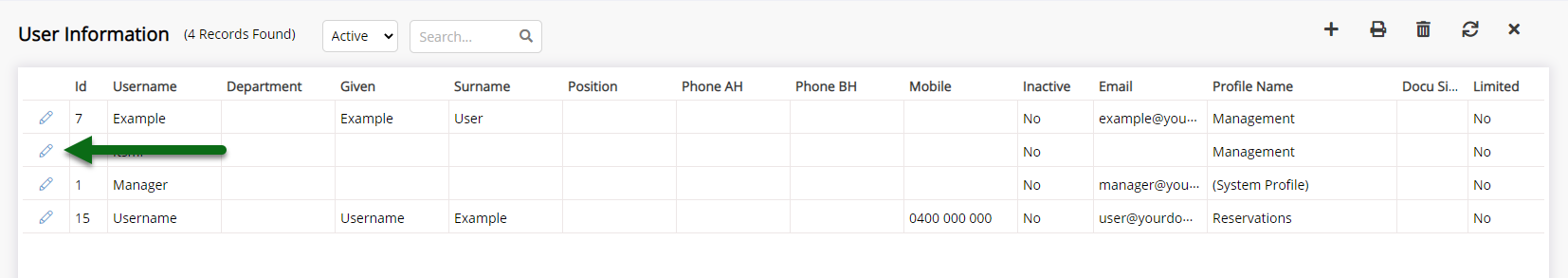
Review the list of displayed users and set any that should not have access to RMS as 'Inactive'.
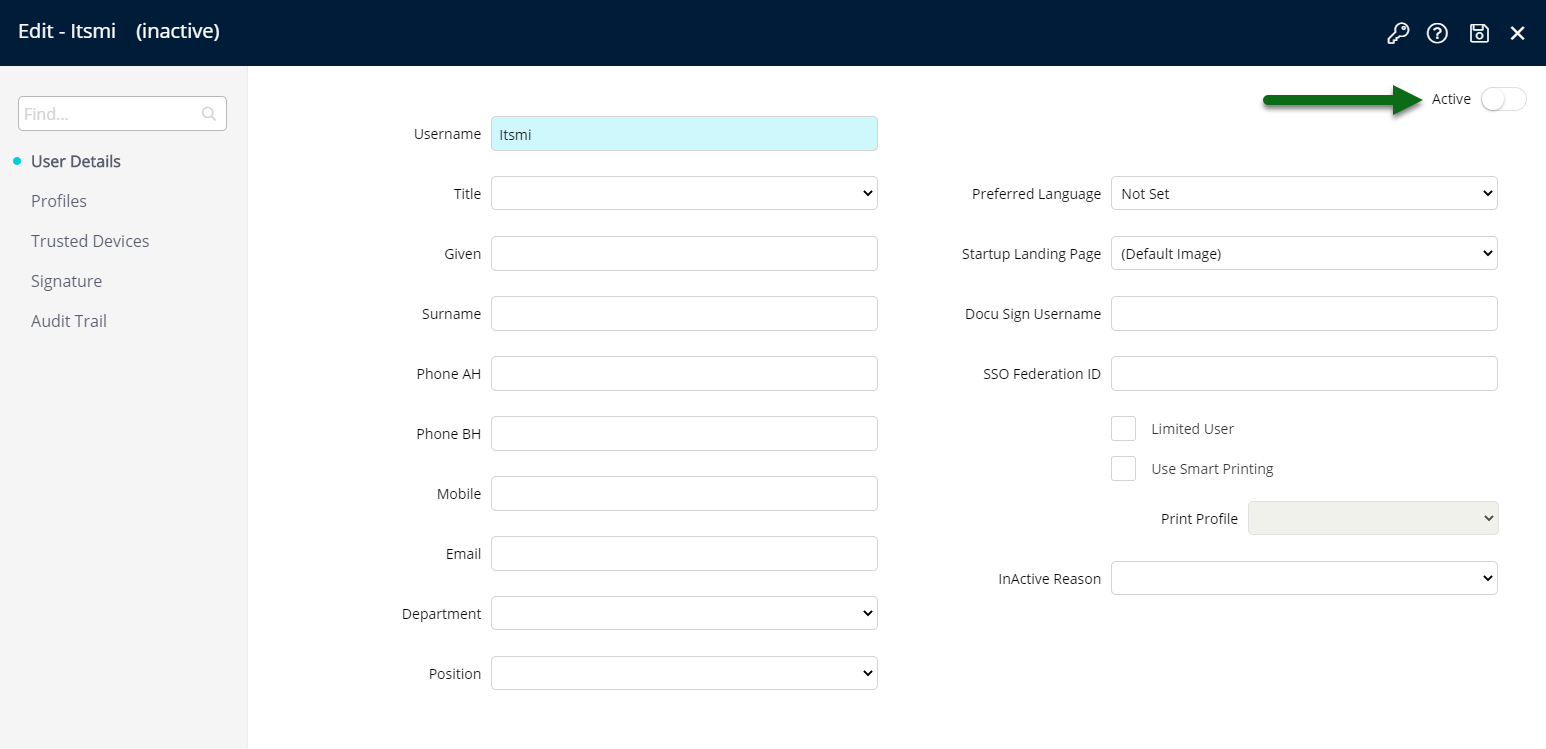
To set a user 'Inactive' select 'Edit' on the identified user, set the 'Active' toggle to the off position and choose 'Save'.
-
Next
- Add Button
Security Profiles
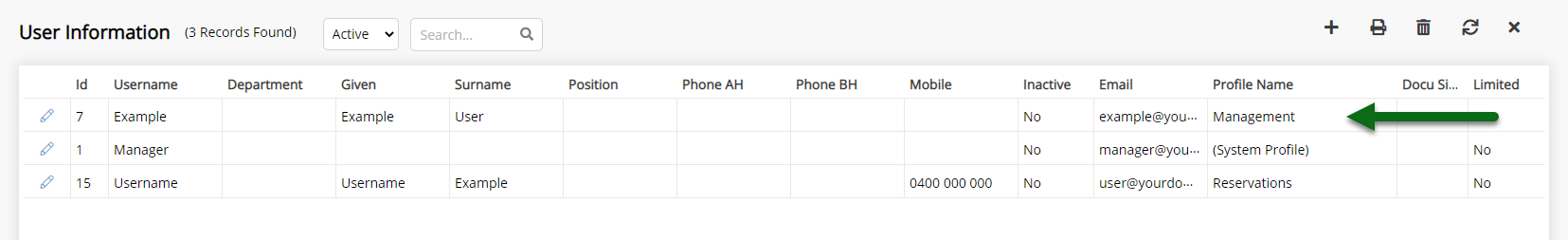
Review the level of access each active User has in RMS by checking which Security Profile is assigned.
The 'Profile Name' column on User Information setup will list all Security Profiles assigned to that user and can be used to quickly verify the Security Profile assigned still matches the staff member's role at the property.
Enterprise customers may choose to 'Edit' a user and review the Properties & Security Profiles a user has access to on the 'Security Profile' tab.
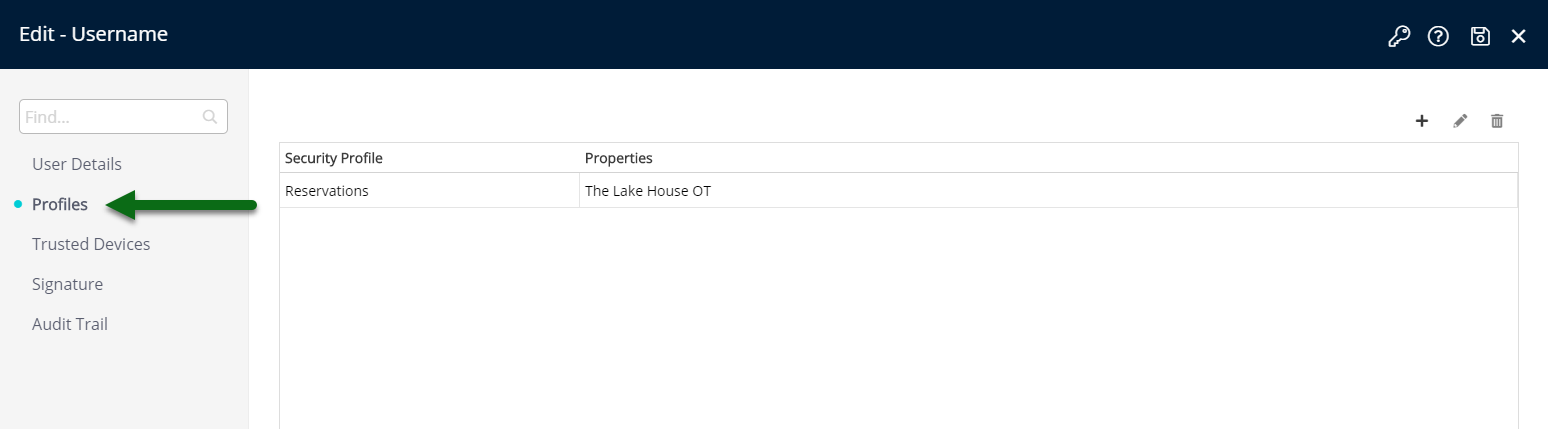
Users should only be assigned a Security Profile with the access level required to perform their duties.
-
Next
- Add Button
User Audit
The System Access Report and User Audit Report provide detailed information for user logins and the actions performed in RMS.
Generate a System Access Report for all users and review the login times and IP addresses to verify user access to RMS.
If you notice any unusual activity for a user immediately reset the user password and review the Security setup in RMS.
-
Finish
- Add Button
Finish
An audit of the active users in RMS has now been completed.

Review the Password Policy and enable Two Factor Authentication for an additional layer of security to user login or use Restricted IP Addresses to limit the IP Addresses that can access your RMS database.